Information is an important asset and plays a major role in achieving the business goals of the organizations, which require the development of measures and protection mechanisms. In modern information systems information derived from the processing of digital data stored in information systems, which are shared by different geographical areas.
Information Security Management is an important governance and administration procedure aiming at the protection of an organization from internal and external risks that would negatively affect the achievement of its operational objectives.
Organization’s information systems operate and manage critical data, are called to serve a large number of users and thus they require effective security management.
As a result, specific technical and organizational controls should be identified and implemented in order to ensure the protection of the confidentiality, the integrity and the availability of Organization data.
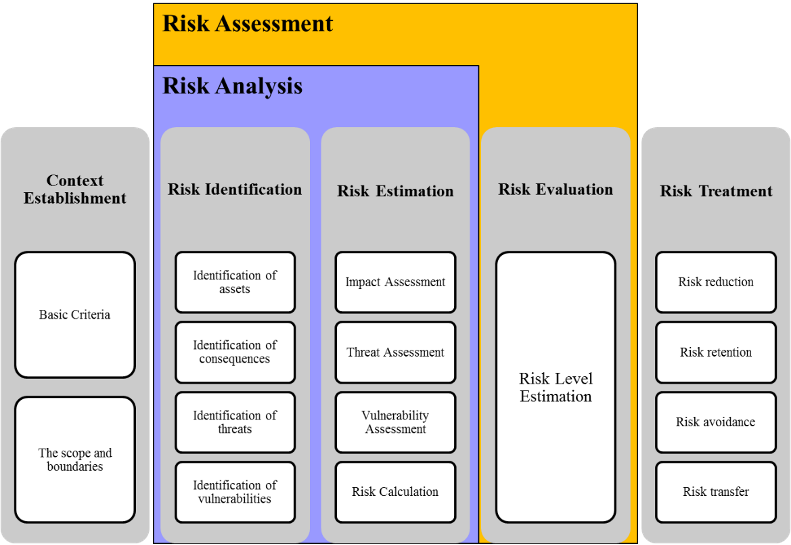
The main goal of the Risk Assessment is the identification and evaluation of risks that the Organization faces. In order to achieve this, a detailed risk assessment should be conducted based on best practices and standards (e.g. ISO 27005, NIST, and other known Risk Assessment methodologies).
Specifically, in order to conduct the Risk Assessment, the following steps are followed:
Phase I – Data & Business Processes Identification: The Data & Business Processes Identification is performed, via workshops in order to identify the data type used for each organization business process. This is conducted with the collaboration of all appropriate Organization personnel.
Phase II – ICT Asset Identification: The Information and Communication Technology (ICT) systems were identified, and the asset inventory is prepared along with the system’s interdependencies.
Phase III – Impact Assessment: In order to calculate the Impact Value for each information asset (data, software, hardware, personnel, infrastructure) the impact for the Organization should be taken into account in case of loss of security (loss of Confidentiality and/or Integrity and/or Availability). Specifically, the evaluation of the security and business continuity importance for each combination of information asset and business process is performed and each information asset is assessed for the impact caused due to the violation of a security property (i.e. loss of confidentiality and/or integrity and/or availability) considered different scenarios and consequences. The indicative scenarios that could be examined are the following:
- Loss of Availability
- Unavailability < 4 hours
- Unavailability < 1 working day
- Unavailability < 2 working days
- Unavailability < 5 working days
- Unavailability < 10 working days
- Unavailability > 10 working days
- Loss of Integrity
- Partially loss of data
- Total loss of data (including backup)
- Deliberate data alteration
- Unintentional Data Alteration
- Loss of Confidentiality
- Disclosure to Insiders
- Disclosure to Partners
- Disclosure to Externals
Phase IV – Likelihood Estimation: The Likelihood is calculated as the combination of the Threat Level and the Vulnerability Level. Specifically, the calculation of the Threat Level, is performed by taking into account the following criteria: {C1: Access to the asset, C2: Actor, C3: Motive, C4: Threat Surface} for each combination of threat and asset.
In order to identify the Vulnerability Level of each asset against the examined threats, the existing controls are taken into account and the level is revealed from the Vulnerability Assessment Scale of the methodology.
Phase V – Risk Assessment: After collecting all appropriate values for Impact, Threat and Vulnerability the Risk Value is calculated for each combination of Asset-Threat-Vulnerability as the product:
Likelihood = Threat Value + Vulnerability Value
Risk Value = Impact Value + Likelihood
Phase VI – Risk Treatment: The proposed countermeasures for each information asset, different for each possible combination asset-threat-vulnerability are identified. The authorised personnel of the Organization should complete the Risk Treatment Plan with the following information:
- Mitigation Action (Strategy): Select the appropriate strategy for each identified risk:
- Mitigate: Implement the proposed controls, The level of risk should be managed by introducing, removing or altering controls so that the residual risk can be reassessed as being acceptable.
- Acceptance: Accept the risk- no further action. The decision on retaining the risk without further action should be taken depending on risk evaluation.
- Transfer: Transfer the identified risk (i.e., via insurance, via service contract, etc.). The risk should be shared with another party that can most effectively manage the particular risk depending on risk evaluation.
- Avoidance: The activity or condition that gives rise to the particular risk should be avoided
- Risk Owner: Define the Risk Owner
- Description for the implementation:
- Details regarding the implementation procedure
- Responsible person for the implementation
- Responsible person for the implementation
- Implementation Time:
- Immediately
- Within next 6 months
- Within one year
- Residual Risk: The risk that remains after the implementation of the strategy. The risk level is according to the Risk Scale of the Methodology.
Project Phases
The following Figure presents the main phases of the project.