STORMTM : Secure Tool for Risk Management
Governance, Risk & Compliance Tool

STORMTM
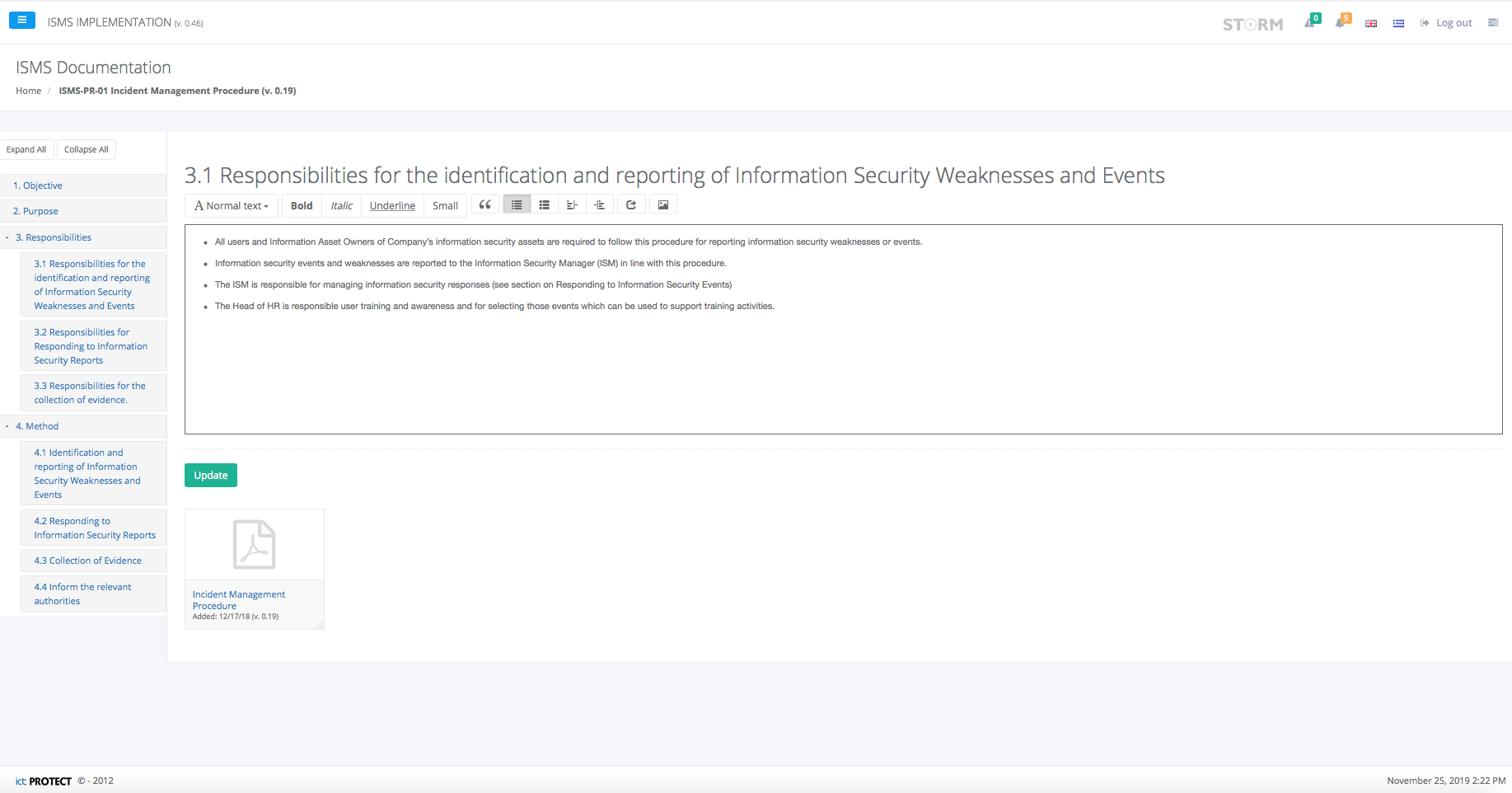
The STORM collaborative environment implements all the phases of STORM-RM methodology and offers them as friendly e-services. Specifically, the collaborative services offered to the STORM users (members of the security team, managers, administrators, end-users) by the STORM environment are:
STORM TM is an innovative, collaborative, cost effective and user friendly security consultancy environment that can be used by different type of organisations in order to collaboratively manage their information security. STORM can easily be parameterised in order to address the needs of different types of Information and Communication Technology (ICT) systems (i.e. critical infrastructures, SMEs).
STORM: A unified platform designed for compliance with industry specific cybersecurity requirements (e.g. ISO 27001, NIST CSF, GDPR, IMO, NERC CIP etc.)
Risk Management Services
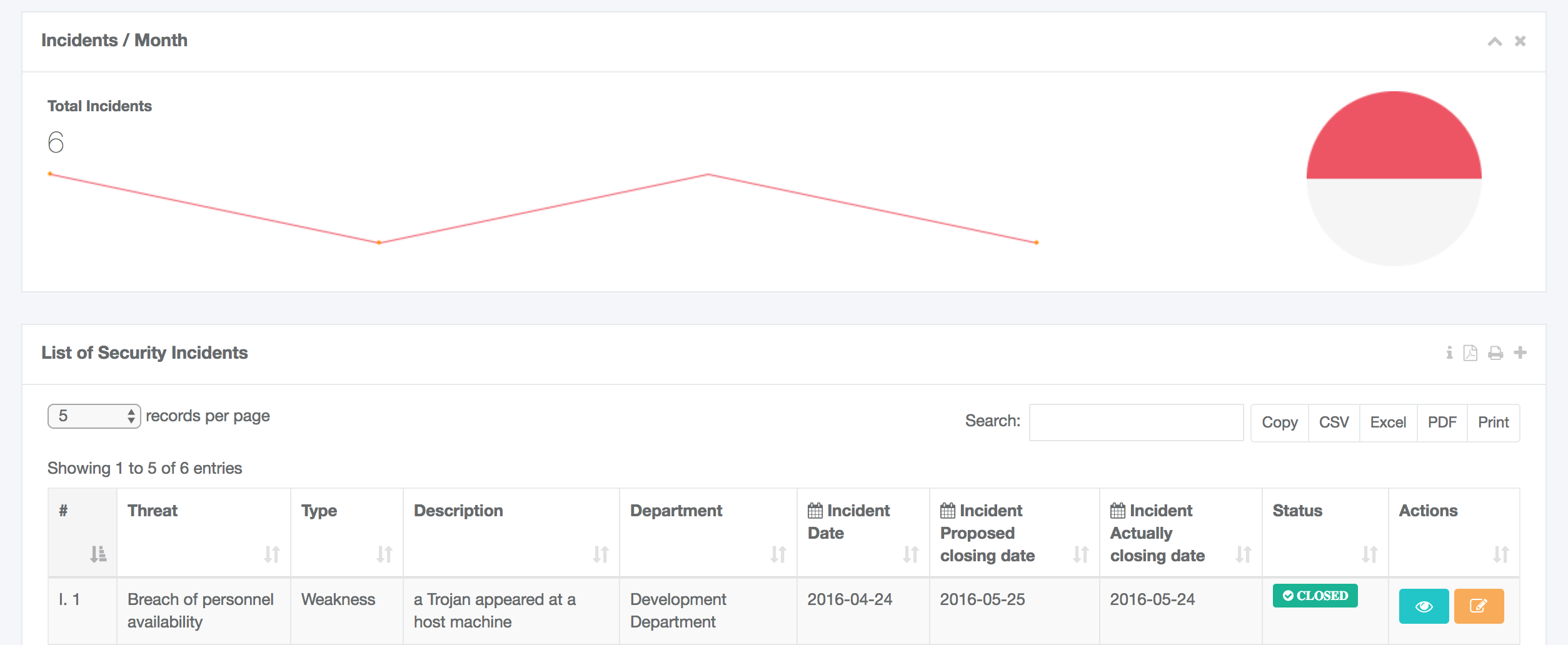
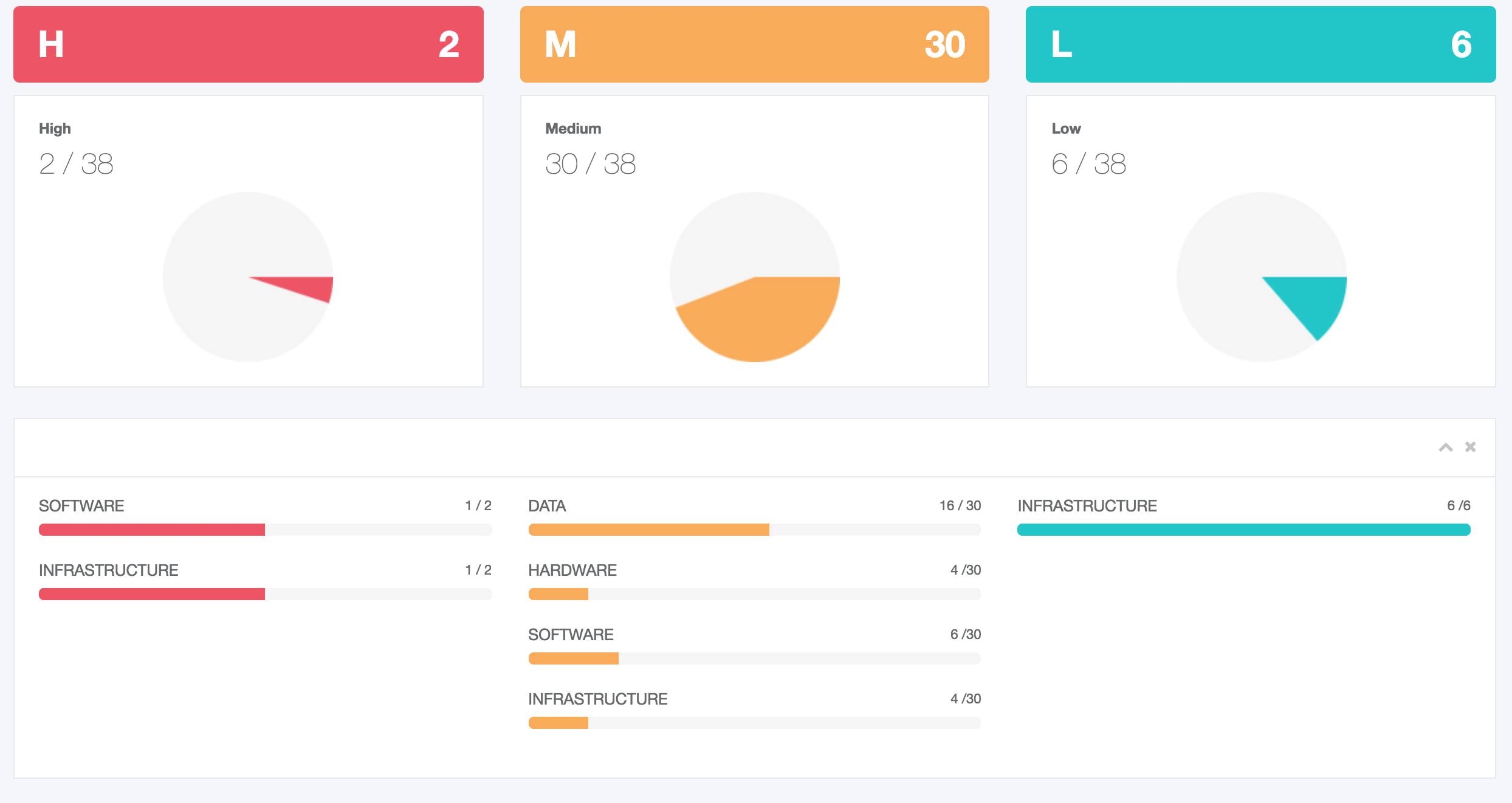
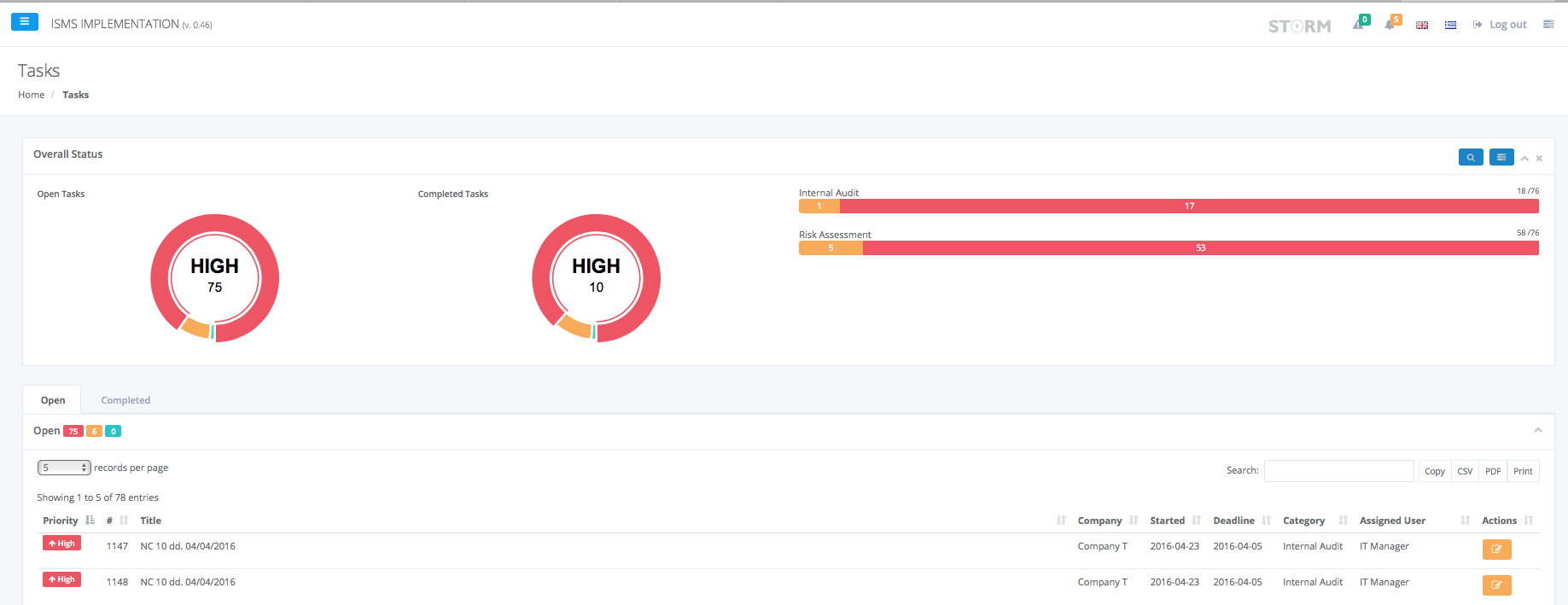
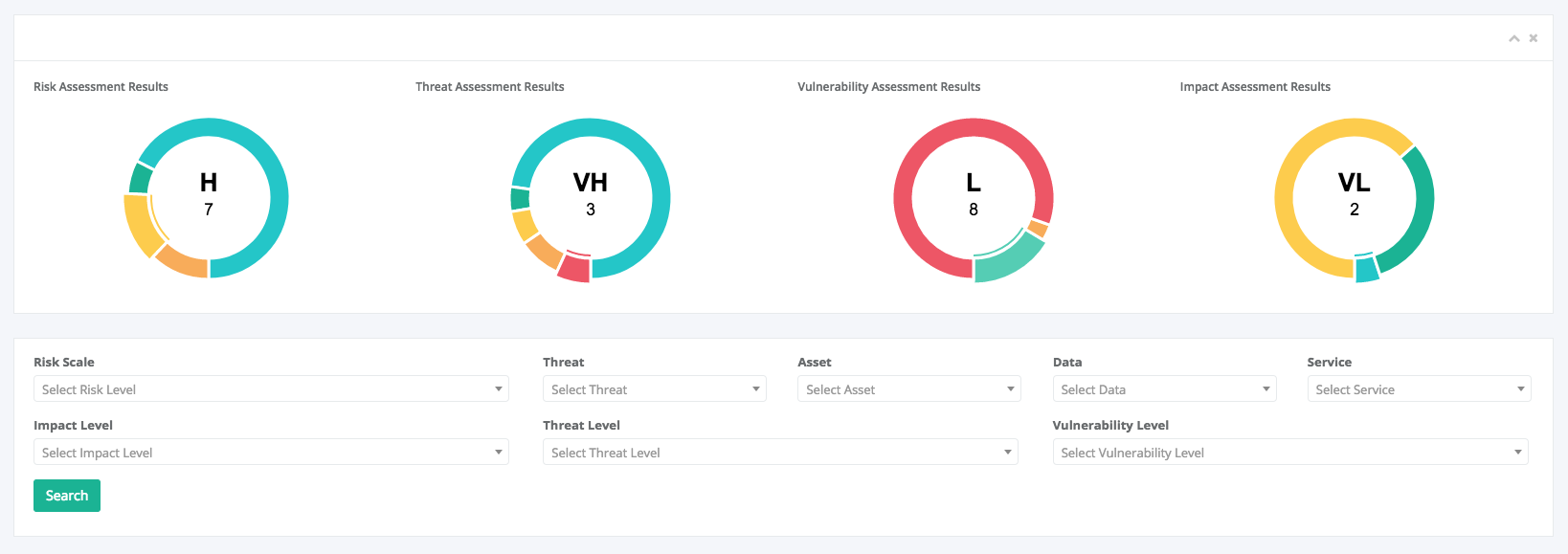
The main goal of this group of services is to conduct the Risk Assessment & Risk management. All the phases of STORM-RM methodology are implemented in an automated, self explanatory, user friendly mode by making use of interactive screens, online forms and help menus.
Security Documents Services
This group of services is responsible for the creation and updating of all the security key documents.
Security Awareness Services (Wiki, Forum, Survey)
The goal of this group of services is to facilitate collaboration and exchange opinions and ideas on Information Security topics as well as to ensure the security awareness.
Via the Forum service, the users are able to find immediate solutions to any everyday security problems and they are able to be constantly informed of the security trends and issues by the use of Wiki.
Via the online Survey and STORM Wiki, you are able to set up security awareness programs in order to ensure that all the organisation’s users are aware of the security policies, procedures and their responsibilities.
Banking & Insurance
Software Houses
Maritime Sector
Governmental Organisations
Cloud Providers
Energy Sector

IS IN OUR DNA.